
Image credit: DALL-E
Recon
It all started during a recon phase on a YesWeHack program, when I came across a rather curious 404 not found page that I’d never seen before :
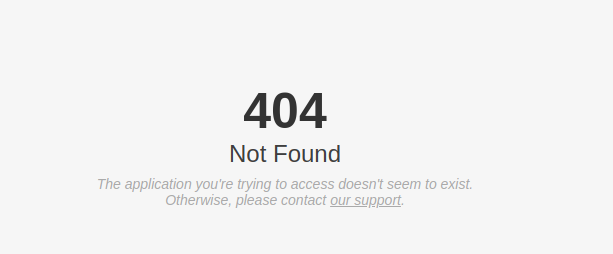
The source code of the page gives us a few indications :
The application you’re trying to access doesn’t seem to exist.
Otherwise, please contact support@clever-cloud.com
Sounds very interesting !
Clever Cloud
Clever Cloud is a French cloud hosting and deployment platform offering hosting services for web applications and online services. It aims to simplify the process of deploying and managing applications by offering a managed cloud infrastructure.
According to Clever Cloud’s documentation, there are two ways to deploy a custom domain: either via a CNAME record (recommended), or via A records :
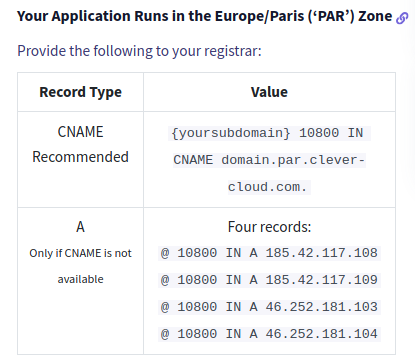
And if we look at the DNS records for our subdomain :
xxx.target.com. 60 IN A 46.252.181.104
xxx.target.com. 60 IN A 185.42.117.109
xxx.target.com. 60 IN A 46.252.181.103
xxx.target.com. 60 IN A 185.42.117.108
This confirms that our sub-domain points to Clever Cloud, with an application that (a priori) no longer exists.
Deploying an application
Clever Cloud offers several options for deploying an application.
In my case, I wanted to go for the quickest and simplest.
1°) Choose the Github account registration option : http://api.clever-cloud.com/v2/github/signup
2°) Once you have created an account, deploy a new application:
- Create => an application
- Choose your Github repo containing the application code
- Choose the type of application: in my case, a simple static web page

- Choose a name, and create
Note : in my case, I had created a new repo on my Github containing a simple index.html :
Hello world !
<! — POC by Supr4s – subdomain takeover –>
Taking control of the subdomain
Once the application has been created, go to its parameters => Domains names => and enter the vulnerable sub-domain in the Custom domain names section.

If you don’t get an error message, you’re all set !

Otherwise, the target is not vulnerable. (You are not allowed to use …)
Enjoy
Having been able to take control, the subdomain now displays the contents of my Github repo :
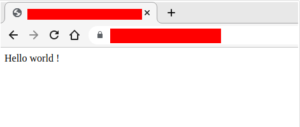
Don’t forget that you can also deploy PHP, Java, Python, Go etc. instead of a simple static web page.
To conclude
For Clever Cloud, we’re on an edge case here depending on what’s been configured at the victim, but if you’re lucky, you’ll get a nice bounty !
Taking control of a subdomain can have a big impact, and you’ll find some great articles on the subject :
- https://www.honeybadger.io/blog/subdomain-takeover/
- https://blog.halosecurity.com/exploring-the-risks-of-subdomain-takeovers/
Sharing with the community
Sharing is the key, I’ve made a Nuclei templatef for this vulnerability : https://github.com/projectdiscovery/nuclei-templates/issues/8697
Enjoy !
